Introduction
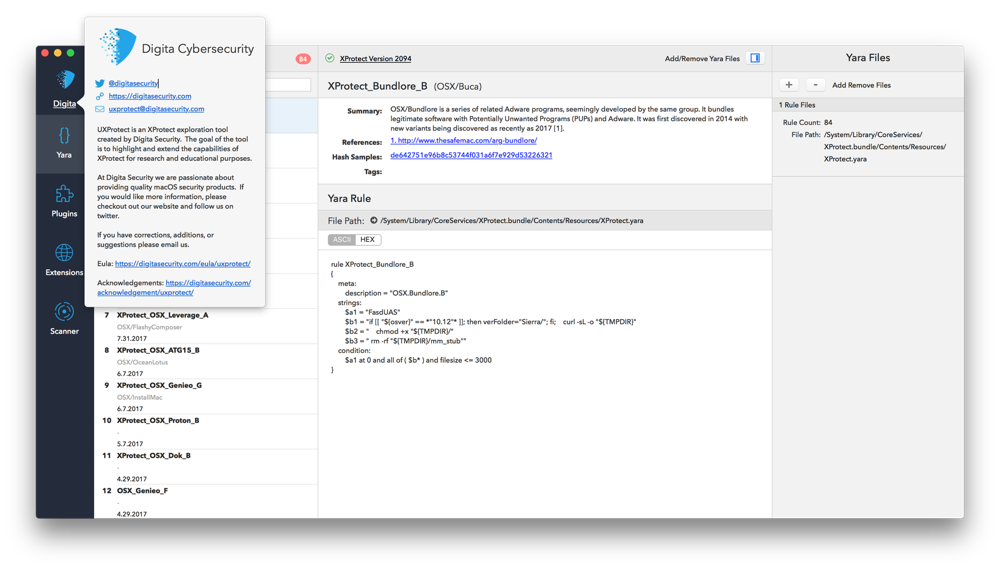
Download
To begin using UXProtect first download the zip archive containing the application. Depending on your browser, you may need to manually unzip the application by double-clicking on the zipped archive. Optionally, drag and drop the extracted application to the location of your choosing (typically the Applications folder).
As of version 1.1 you can also check for updates and install from directly within the app using the UXProtect->Check For Updates… menu item.
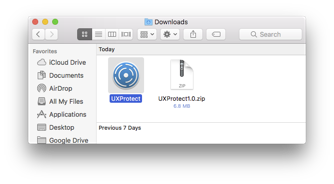
Launch
Presumably, your browser will have set the quarantine flag when you downloaded and extracted the zip (as it does with all downloaded applications), so upon first launch of UXProtect, Gatekeeper will ask if you are sure you want to launch the application downloaded from the internet. Click “Open”.
As an interesting aside, these are the same mechanics utilized to launch an XProtect scan of a downloaded file. For more information on Gatekeeper, check out this great presentation from Objective-See on the internals of Gatekeeper.
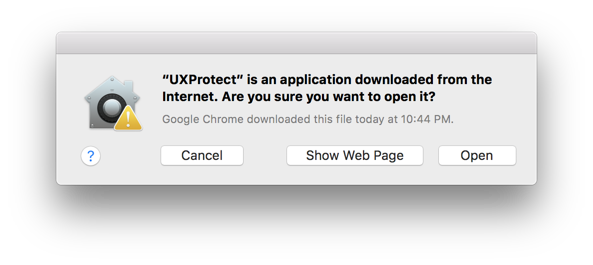
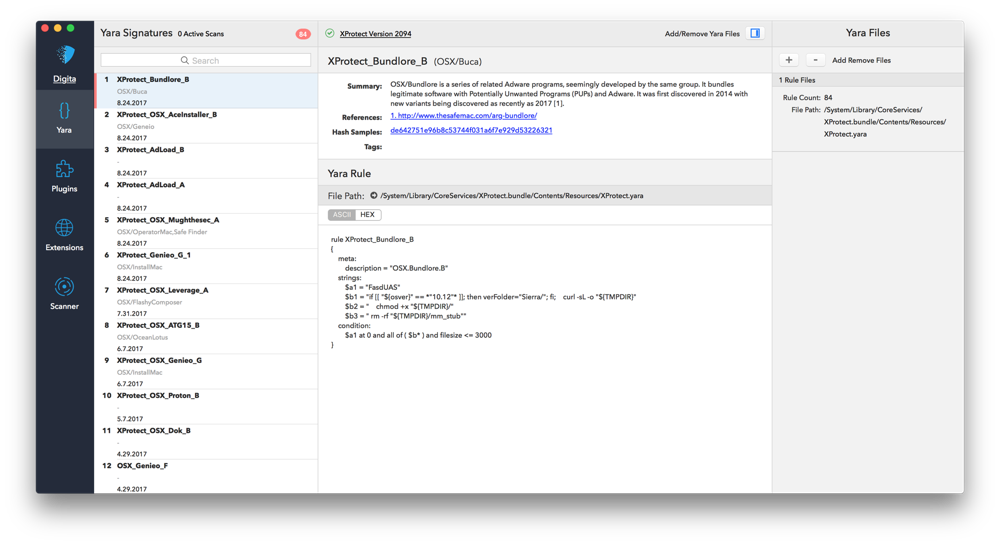
Yara Signatures
Upon launching the UXProtect application, you will be presented with the Yara signature explorer view. XProtect signatures have been parsed and pre-loaded from /System/Library/CoreServices/XProtect.bundle/Contents/Resources/XProtect.yara. From here you can:
- Study/Search the XProtect pre-loaded signatures to get a sense for the threat and protections.
- View the summary information for each threat and rule
- Explore any linked references for more specific information on each threat
- Explore specific samples of the threat by visiting VirusTotal (by clicking linked Hash Samples)
- Toggle between the ASCII converted rule strings, and the HEX representation (note: not all rule strings cleanly convert to ASCII, depending on the rule).
- Add and remove additional Yara Signatures into the explorer and scanner (see below) using the slider on the far right.
For an introduction, or refresher on Yara rules, visit Writing Yara Rules.
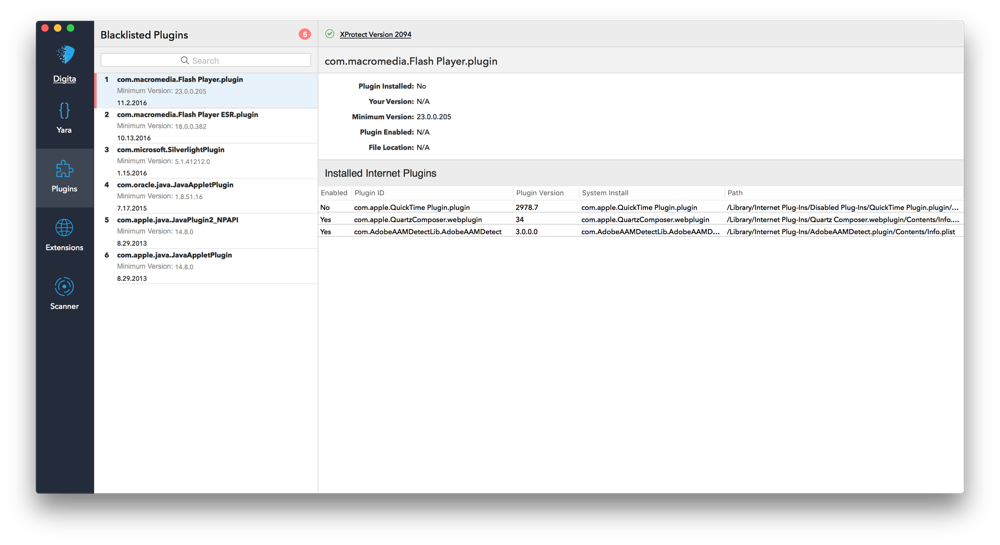
Plugins and Extensions
UXProtect also highlights information about the plugins and extensions that are blacklisted by XProtect. Both lists are parsed
from /System/Library/CoreServices/XProtect.bundle/Contents/Resources/XProtect.meta.plist and displayed in a more user friendly way.
Additionally, UXProtect presents information about other loaded plugins and Safari extensions on your computer.
- Installed plugins are parsed from
/Library/Internet Plug-Ins/and~/Library/Internet Plug-Ins/ - Installed extensions are parsed from
~/Library/Safari/Extensions/Extensions.plist
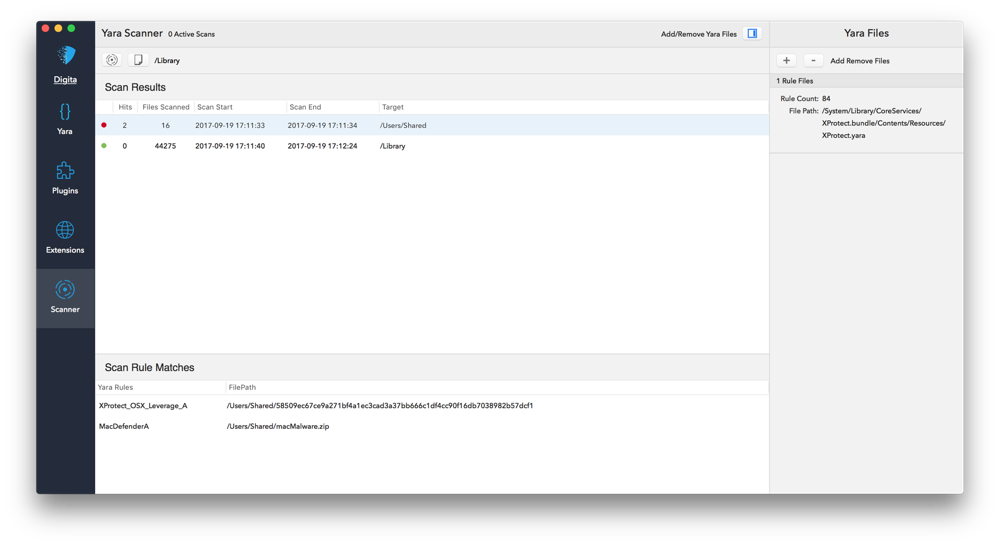
Scanning
As we noted in the “Launch” portion of this guide (and will cover more extensively in an associated future blog post), XProtect will scan a file downloaded from the internet, once launched or opened, if the downloading application sets the Quarantine flag on the download. UXProtect will leverage the same Yara rules (under)utilized by XProtect to extend the scanning capabilities to include on-demand scans of any file or directory on the file system. Additionally, you can load additional custom or community defined Yara rules using the expandable section on the far right of the tool.
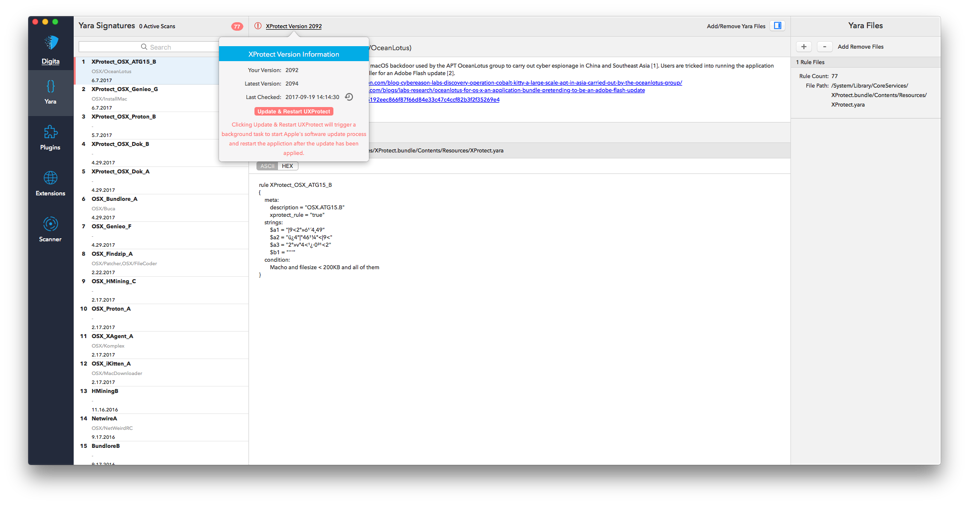
Signature and XProtect Configuration Updates
One of the smaller, but neater features of UXProtect is the ability to selectively and immediately force an update of available XProtect configuration data (i.e. updated Yara signatures) as new threats are addressed by Apple. Other update methods documented on the web fell short for a variety of reasons. They require elevated privileges, automated updates to be enabled, and/or installation of all similarly available packages. While developing UXProtect, we discovered an undocumented option to the softwareupdate application that overcame these issues, and gives complete control to the administrator/user as shared in this tweet.
The commands used to perform the update are:
softwareupdate -l --include-config-datasoftwareupdate -i XProtectPlistConfigData-1.0 --include-config-dataUXProtect is able to leverage this same technique to force immediate XProtect signature updates.
Using in headless mode from the command line
As of v1.1, UXProtect supports running select features from the command line without launching the UI.
Usage:
$ UXProtect.app/Contents/MacOS/UXProtect -h Usage: UXProtect [options] Options: -g, --getVersions Get the currently installed and available XProtect Versions -f, --forceUpdate Force an update to the latest available version -h, --help Show this help message and exit
GetVersions example:
$ UXProtect.app/Contents/MacOS/UXProtect -g
{
"current" : 2098,
"available" : 2098
}
ForceUpdate example:
$ UXProtect.app/Contents/MacOS/UXProtect -f
{
"msg" : "Already up to date",
"pre" : 2098,
"post" : 2098
}
Networking Considerations
UXProtect only establishes requests to Digita enrichment and update resources hosted on it’s website, to Apple to perform XProtect update checking, and to send diagnostics to our Sentry.io resources in the case of fatal application errors. UXProtect uses the enrichment data to enrich Yara signatures, blacklisted plugins, and blacklisted extensions with additional information. If UXProtect is unable to connect to these enrichment resources at application launch it will use a local (perhaps outdated) copy packaged within the application bundle.
FAQs
Q. Why is UXProtect failing to update XProtect from v2094 to v2095 configuration after a High Sierra update?
A. This appears to be a bug in the High Sierra Updater/Installer that is simply being highlighted by UXProtect. For more details, including a possible mitigation, see our blog post on the topic.
Feedback? Suggestions? Corrections?
Please email us at UXProtect@digitasecurity.com or submit a new issue
Updated January 2018 for v1.1